
Get Your Vulnerability Assessment and Penetration Testing (VAPT) Done In 3
Days. Starting From Just $3000/Target.
Need a quote in the next 24 hours?

Apply For Your VAPT Quote Now
Our Feature
Why Work With Privacy Ninja?


Look at our Track Record
We founded Asia’s first bug bounty platform and have been keeping Organisations, MNCs and SMEs all over the world safe from cyber attacks, security threats, critical vulnerabilities, and data breaches.
Large organisations like A*Star Research, Marché, E27, MightyJaxx, AlphaWave trust us with their penetration tests and cyber security.
Not one of the companies we’re working with have suffered a data breach after engaging us.

Our team is made up of the best penetration testers in the world
Our pentesters are hall of famers who have ethically hacked the most secure systems in the world like Microsoft, Google, Facebook, etc.
With an unparalleled knack for uncovering security vulnerabilities, network security attacks, and security threats, there's nothing our pen testing team haven't seen. They identify vulnerabilities for breakfast.
We complete our Vulnerability Assessments and Penetration Testing (VAPT) within 7 days of project commencement, ensuring stringent safety procedures are adhered to while conducting vulnerability assessments, vulnerability analysis and vulnerability testing, especially for web applications.

Despite being the best in Singapore, we’re the most affordable
We pride ourselves on being the best pen testing provider in Singapore, but are also 100% committed to being the most affordable.
Price beat guarantee! If you find a price with another licensed pentesting provider that’s cheaper than you can get from us, we’ll beat it by 20%. Plus, your 2 x revalidation is on us!
Our Double Guarantee

20% Price Beat Guarantee
Annual VAPT is mandatory to identify vulnerabilities for all networks, mobile, and web apps that store sensitive data including personal data in data bases.
This is among the security measures adopted by companies who are serious about their cybersecurity posture. We believe businesses shouldn't have to pay extra to stay compliant and avoid penalties.
If you find a lower price with another licensed VAPT service provider, for the same scope of work or more, we'll beat their price by 20%. Terms & Conditions apply.

Our Security Guarantee: Unlimited Revalidations Until You’re Fully Secure
We’re not just affordable — we’re trusted. None of our clients who used our VAPT services have ever been hacked, and we’re committed to keeping it that way. That’s why we offer a 1-Year Unlimited Revalidation Guarantee: unlimited revalidations for a full year after the initial test, at no extra cost. While others charge for revalidations , we don’t stop until your systems are completely secure. Because if we can’t help you stay protected, we don’t deserve your trust. Terms & Conditions apply.
We are Featured In

Affordability is one thing. A solid report is everything.
Complete Your Vulnerability Assessments and
Penetration Tests With Privacy Ninja in 7 Days
After the VAPT exercise, all findings will be detailed in a report that includes
Overall findings summary
Itemised replicable steps/ POC (Proof-of-concept)
Explanations
Vulnerability impact
Common Vulnerability Scoring system (CVSS) risk rating
Practical recommendations for remediation
Our Pentesters' Certifications

CSRO License (Entity): Privacy Ninja Penetration Testing Service License No. CS/PTS/C-2022-0128R
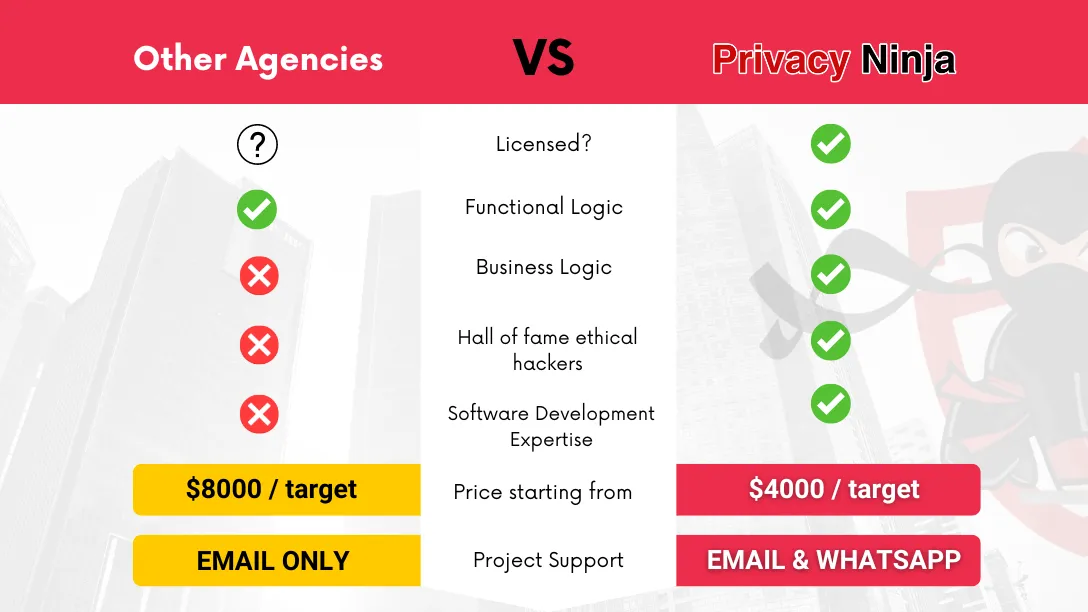
Other Agencies VS Privacy Ninja
Our Services
Industries We Serve






Proven Results For A Wide Range of Clients
Our Clients

Testimonials
What client say about us


CHANG WHEI FERN
Finance and Admin Manage
of Marché Restaurant
Privacy Ninja is always ready to address any of our PDPA compliance requirements. They were also swift to assist when we require advice on ramping up our cyber security needs.
The VAPT service provided was quick and insightful which helps to understand and improve on our internal network security.

RODNEY YAP
Founder of UserTip
Privacy Ninja's team was quick to finalize the security assessment scope and advised on what we needed to test. Initial findings report was delivered early that heled us secure our application before going live.Trusted & Affordable!

Tjia Jinhang
Admin & Operation Manager of
Kingsforce Management Service
Working with Privacy Ninja gave us peace of mind. They are professional at work, gave quick inputs and good advice. We are assured of having a strong Cybersecurity firm behind us everyday.

DANIEL CHAN
Director of Professional
Services at Ascent Solutions
Working with Privacy Ninja was a breeze. They were very clear, professional, and flexible in the way that they work. Great team!

Jun Hong
Senior System Admin at
SICS A*Star
Seamless experience from onboarding to project delivery. Each step is clearly disclosed and well taken care of. Privacy Ninja is accommodating to our timeline & enquires. They don't hesitate to provide extra services if they find vulnerabilities even if it's beyond the SOW. We met our project objectives, deadlines & budget. I recommend Privacy Ninja to anyone who wants a trusted VAPT vendor or outsourced DPO.

Here’s what you’ll get in this FREE VAPT Quote:
Identify the most suitable and recommended type of security assessment for your project so you do the right thing and don't overpay for what you don't need.
Receive detailed sample related reports to your project so you know what to expect in the report and ensure that it's something you understand and are able to work on.
Quotation with the only price beat guarantee in the market so that you get the most affordable vulnerability assessment and pentesting on top of the best pen testing team.
Apply For Your VAPT Quote Now
© 2024 Privacy Ninja Pte Ltd. All rights reserved